About Me
My Projects
Active Directory Lab
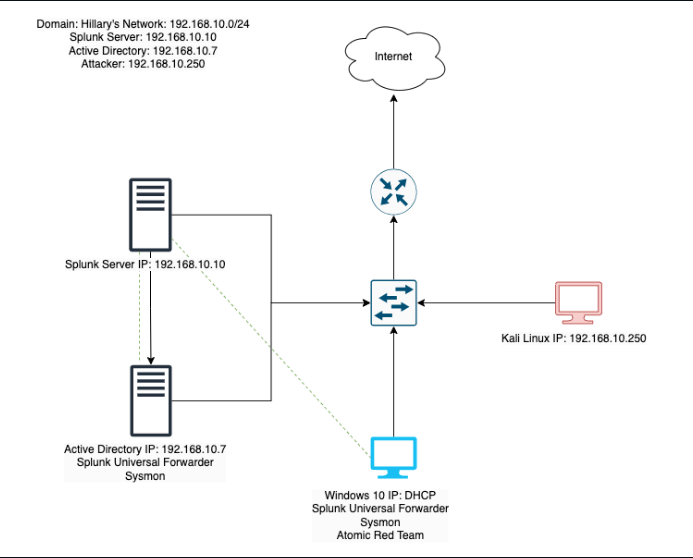
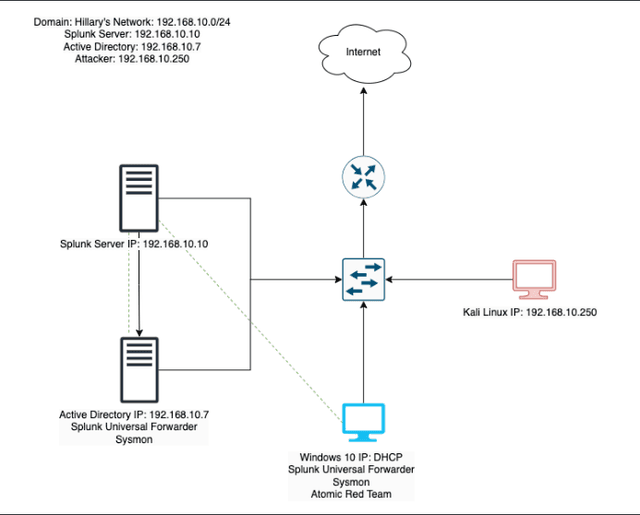
This project involves setting up a home lab environment using VirtualBox to simulate a small Active Directory infrastructure with two Windows 10 machines, a Kali Linux machine for penetration testing, and a Splunk machine for telemetry and log analysis. The environment was configured to simulate security attacks on an Active Directory domain, collect telemetry data, and analyze potential vulnerabilities.
Click here to checkout the blog post- active directory
- windows server
- GPO
- powershell
- splunk
- crowbar
- atomic red team
- ubunto
- kali linux
- sysmon
SOC Automation Lab
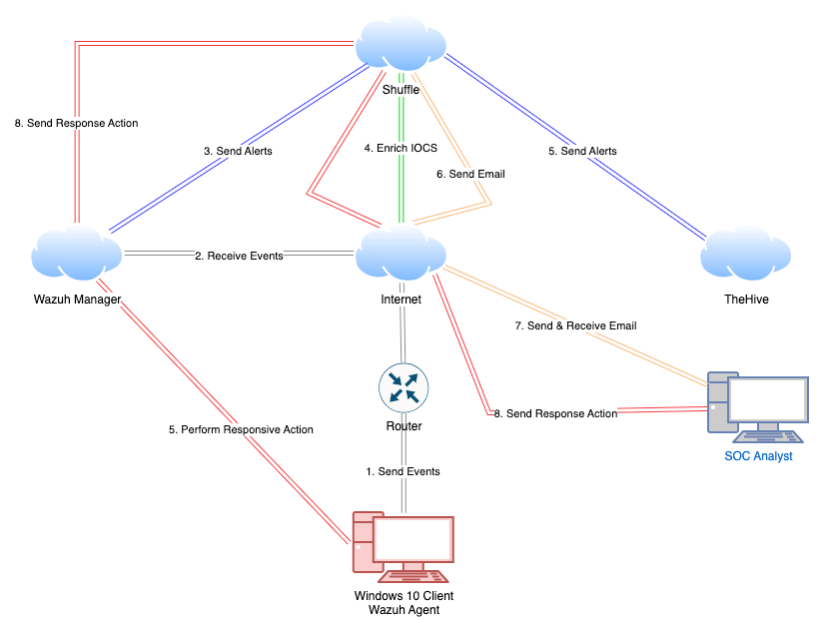
The SOC Automation lab aims to automate a Security Operations Center (SOC) that streamlines event monitoring, alerting, and incident response. You can create an efficient and resilient SOC by leveraging powerful tools such as Wazuh, TheHive, and Shuggle. This lab was inspired by the Youtube Channel MyDFIR.
- Wazauh
- shuffle
- TheHive
My Skills
- Active Directory
- Jira
- Windows 10
- Microsoft Exchange
- Office 365
- Troubleshooting
- Cisco AnyConnect
- Duo Mobile
- Server 2016
- Server 2019
- Vmware
- Splunk
- Kali Linux
Featured Blogs
Here are some of my latest blogs, where I share my thoughts on various topics related to cybersecurity, personal projects, and tech. I hope you find them insightful and engaging! Feel free to leave any feedback by reaching out through the contact form.
Active Directory Lab
Published on 7/21/2025
From Theory to Practice
Theory only gets you so far, especially in the cybersecurity field. Without application, it’s easy to feel like an imposter. Studying for my Security + gave me a solid foundation. I learned what a SIEM is, but I didn’t truly understand how to work with logs in a platform like Splunk until I started exploring it myself. That realization pushed me to build a home lab where I could apply what I’d learned in a safe, controlled environment.
I also know how competitive the job market is, and how often employers prioritize experience over potential. I believe in my ability to learn anything I set my mind to, but I understand that belief alone isn’t enough. That’s why this lab is more than just a personal project. It’s my way of showing, not just telling, what I’m capable of.
Inside the Lab
This project involves setting up a home lab environment using a virtual machine (VirtualBox in my case) to simulate a small Active Directory infrastructure. My VirtualBox consisted of 4 machines: two Windows 10 machines, a Kali Linux machine for penetration testing, and a Splunk machine for telemetry and log analysis. The environment was configured to simulate security attacks on an Active Directory domain, collect telemetry data, and analyze potential vulnerabilities. Essentially, these tools will give me the ability to explore both sides of cybersecurity: offense and defense, attack and response.
What I Wanted to Learn
The main goal of this lab was to understand how different systems interact. I wanted to see how I could launch an attack using Kali Linux as a red teamer, and then switch perspectives to detect and analyze that same attack as a blue teamer. I also wanted to explore Active Directory by practicing IAM, setting user permissions, and simulating common help desk scenarios. I wasn’t trying to fully simulate a corporate network (not yet). This project was about exploring how cybersecurity, system administration, and hands-on problem-solving all connect in the real world.
The Wins & Challenges
The rumors are true! Following through on what you said you’d do really does help ease imposter syndrome. As a lifelong learner, there’s something deeply rewarding about finally getting hands-on with the tools I used to only read about. It’s the kind of momentum that makes me want to keep building.
I combined “Wins & Challenges” into one section because, to me, every challenge is an opportunity to learn, which I count as a win.
One of the first challenges I faced was performance. My virtual machines were lagging badly. I’m working with an older computer that doesn’t have much storage, so I decided to invest in an external SD. After researching how to safely move all my VirtualBox files to external storage, I finally got everything running more smoothly, and freed up space to continue expanding my lab environment in the future.
Another challenge was configuring a static IP for my Splunk server. By default, VirtualBox assigns dynamic IPs, which means a machine’s IP address can change every time it restarts. That causes problems for systems trying to talk to each other. Setting static IPs not only makes communication between machines consistent, but it also simulates how networks are built.
For Splunk, I ran into an issue where the configuration file I had didn’t match the one used in the tutorial I was following. As a result, my static IP wouldn’t persist after rebooting, it kept reverting to DHCP. After digging through Stack Overflow and Reddit, I learned I needed to create a custom network interface and bind it to the static IP. It took some trial and error, but I eventually got it to stick across reboots.
That moment, when it finally worked, meant more than just solving a networking issue. It reminded me that tutorials can only take you so far. Systems evolve, documentation gets outdated, and eventually, you have to rely on your own ability to troubleshoot. I genuinely believe that the best learning happens when you can’t find an exact guide, and you figure it out anyway.
That feeling? That’s a win.
Looking Forward
I’m excited to keep building on the foundation I’ve laid with this home lab. One of my next goals is to integrate cloud services with either Azure or AWS to create a hybrid environment. I’m also currently learning Python with the hope of automating some of the repetitive processes in my setup.
This project has given me a solid starting point, and I’m proud of how far it’s come, but I know there’s still so much to explore. I’m always open to any suggestions, feedback, or ideas to help me grow this lab or figure out what to build next.
If you’d like a more in-depth, step-by-step guide on how to set everything up, feel free to take a peek at my GitHub.
My Experience
Business Development
Peoples Trust Insurance
- Conducted thorough testing of flood insurance quoting systems to ensure functionality and accuracy.
- Documented detailed findings and reported bugs to the development team for resolution.
- Provided customer support via phone and chat, assisting agents with setting up accounts and generating flood insurance quotes.
- Collaborated with cross-functional teams to enhance quoting system features and improve user experience.
- Maintained organized records of customer interactions and quote histories to streamline follow-up processes.
- Created SOPs for various aspects of the project, including testing protocols and customer support guidelines.
- Contributed to the growth of a new project in a developing market, leveraging limited resources effectively to achieve project goals and milestones.
Data Analyst
Peoples Trust Insurance
- Conducted ad-hoc data analysis to support various departments in identifying business opportunities and potential areas for improvement.
- Prepared comprehensive reports and presentations summarizing analytical findings, leading to data-driven strategic planning.
- Monitored data trends and outliers, investigated, and resolved data inconsistencies to maintain data quality standards.
- Demonstrated strong analytical and problem-solving skills in identifying root causes of business challenges.
Bachelor's Degree, International Business
Florida Atlantic University - College of Business
2021Accounts Payable & Receivable
Peoples Trust Insurance
- Managed the receipt and deposit of checks within established procedures.
- Processed vendor invoices for payment in a timely manner.
- Utilized spreadsheet software to develop and maintain financial records.
- Addressed payment issues and inquiries within the designated authority, conducting research as needed for resolution.
Contact Me
Feel free to reach me directly at hilaryrobles96@outlook.com or through this form.